UL Solutions is an independent global safety science company whose mission is to make the world a safer place. We empower trust by helping you make possible the safe adoption of innovative new products and technologies.
You may expect that any connected product you can buy in a store or online is secure, but in reality, there is no easy way to understand the level of security embedded in a product. Until now.
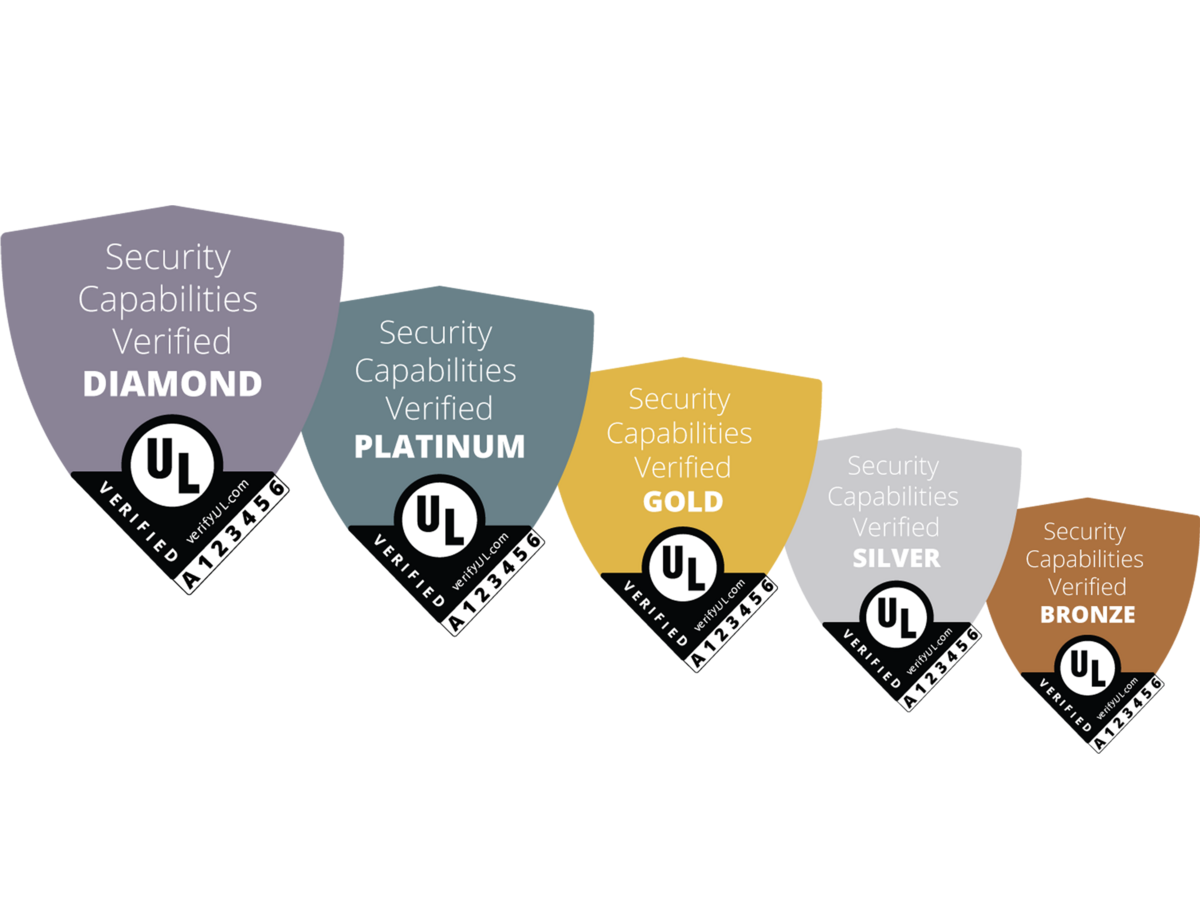
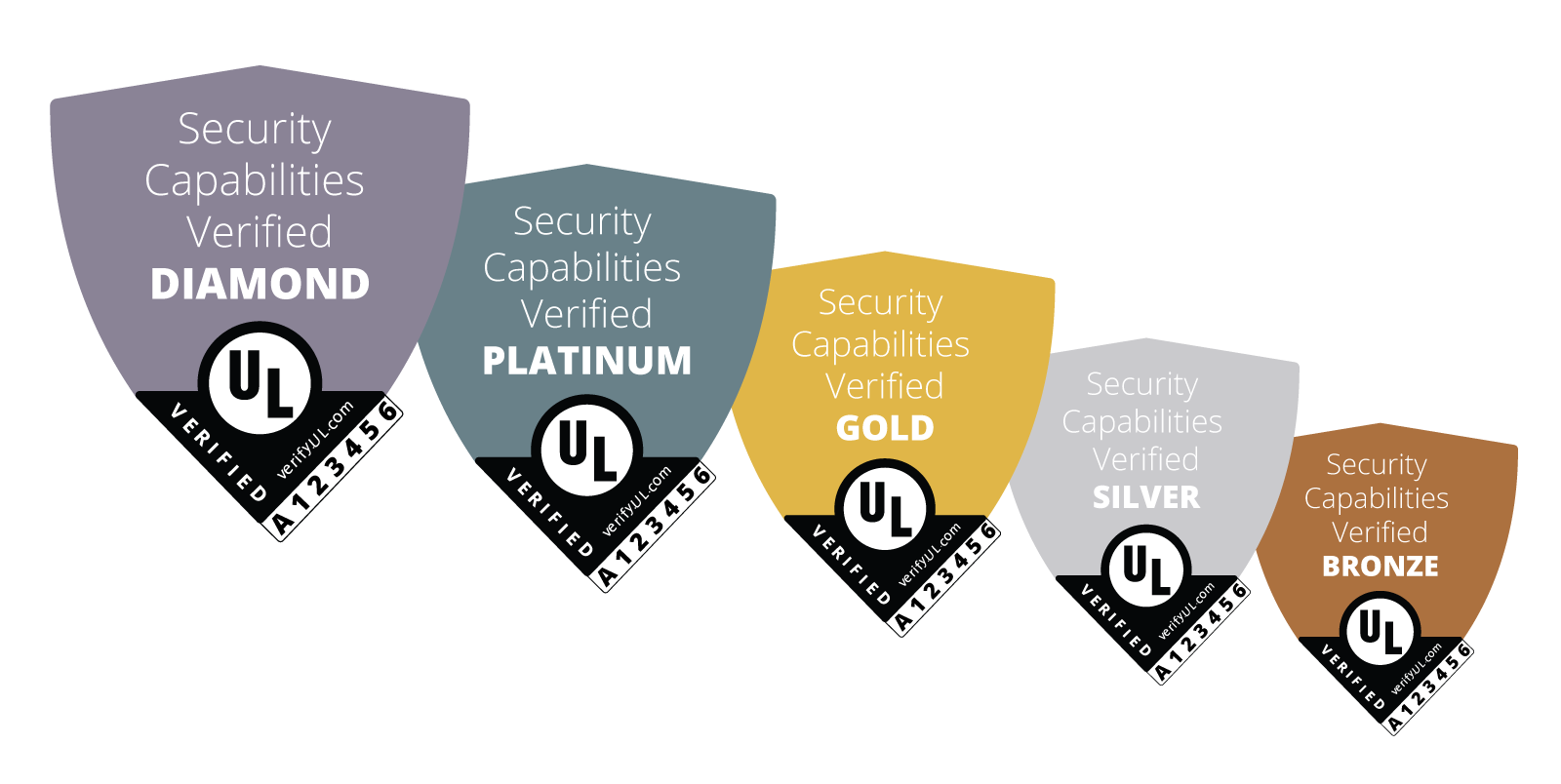
UL Solutions has created a rating system that verifies the security features of connected products. With this UL Verified loT Device Security Rating, our security experts assess products and rate them for one of five security levels, ranging from the lowest level, Bronze, to the highest level, Diamond.
Each level represents a set of security capabilities that is implemented in the product by the manufacturer. A Bronze rating contains a set of essential must-have security capabilities; a Silver contains enhanced security capabilities; a Gold contains more advanced security capabilities; and so on. You can find more details for each of the levels below.
The rating is displayed through the UL Verified Mark and this Mark contains a unique identifier — the number on the bottom-right of the Mark — for each verified security claim. With this identifier, you can look up whether the UL Mark is active or whether it has expired*.
*When no results are found with the identifier you provided, the UL Verification has expired and we have already removed it from our database.
Security capabilities by level
Bronze - Essential

No default passwords
Users don't have to rely on default passwords preprogrammed into a product. Users are instead urged to choose passwords that are difficult to guess/crack.
Secure update mechanism
Regardless of the method of software update — on-demand or automatic — the updated files are validated and confirmed to be secure by the device manufacturer or its software vendor. It is also necessary for the files to be protected by additional authentication mechanisms.
Secure reset
The factory reset button or function securely removes all sensitive data.
Secure connections
Any communication connections being utilized by the device are validated and confirmed to be secure by the device manufacturer or its software vendor.
Silver - Enhanced

Access control
Access to features that hold sensitive information, i.e. security settings and personal information, are protected by additional authentication mechanisms.
Industry privacy best practices
The type of data that is collected, processed and stored by the the device is made known to the user, and the user is given the opportunity to consent to such collection, processing or storage.
Product security maintenance
The device is monitored and maintained for security concerns after-sale of the device.
Gold - Advanced

Stored and transmitted data security
When data is stored or transmitted to the device, the data is secured by using industry-supported encryption.
Secure out-of-the-box settings
The device is secure and ready for use without unnecessary intervention by the user.
Mobile app security maintenance
If a device connects to an app, the app itself is monitored and maintained for security concerns.
Platinum - Extensive

Known threat testing
The device and its software have been tested for publicly known threats.
Malware protection
The device doesn't automatically accept and respond to untrusted code.
Permanent log-in prevention
A user is not able to remain logged in for an indefinite amount of time. The system will intermittently re-authenticate the user.
Diamond - Comprehensive

Malicious software modification detection
The device is able to detect if foreign code is being inserted into its system and prevent that code from altering the device.
Illegitimate access attempt protection
The device protects against repeated failed log-in attempts.
User data anonymization
Data that is processed, collected and stored is kept in a format which will not lead to the identification of the user.
Get in touch
Have questions, need specifics? Let's get this conversation started.