With the introduction of cybersecurity to the Radio Equipment Directive (RED) (2014/53/EU, Commission (EU) 2022/30 and Amendment (EU) 2023/2444) in Article 3.3(d), (e) and (f) of the RED, which is in effect as of Aug. 1, 2025, many household appliance manufacturers have completed or are near completion of their cybersecurity compliance requirements.
These requirements mandate that products with radio functionality, including smart thermostats, home electronics, industrial machines and connected home appliances, must incorporate network protection, data security and fraud prevention measures. To achieve compliance, manufacturers have implemented different conformity assessment options.
Self-declaration vs. notified body assessment: Choosing the right compliance path
Self-declaration: Manufacturers have the option to fully implement the harmonized standards as published in the Official Journal of the European Union.
- EN 18031-1:2024 – Common security requirements for internet-connected radio equipment (Article 3.3(d))
- EN 18031-2:2024 – Security for childcare radio equipment, toys and wearable radio equipment (Article 3.3(e))
- EN 18031-3:2024 – Security for radio equipment processing virtual money (Article 3.3(f))
This route provides benefits to manufacturers that include no need for third-party assessment, faster time to market and lower cost. However, it also comes with risks, as manufacturers need the technical expertise and knowledge to fully comply with the harmonized standards and have the ability to defend their products’ security posture should a surveillance authority ask questions.
Notified body assessments: If a manufacturer does not or cannot fully apply the harmonized standards, they must submit their product to a notified body for a formal conformity assessment. Alternatively, should the manufacturer need guidance, support or expertise while working through third-party laboratories, the notified body can also provide the necessary assurances when issuing a type examination certificate (TEC), as they independently assess whether the product meets essential requirements of the RED.
The benefit of providing alternative technical options and having third-party attestation provides enhanced compliance for surveillance authorities, as it requires detailed technical documentation and testing aligned to the requirements.
Beyond RED: Preparing for the Cyber Resilience Act
Despite meeting RED requirements, it’s not the time for manufacturers to relax. While RED compliance laid the groundwork, the Cyber Resilience Act raises the stakes — demanding continuous cybersecurity oversight and expanding responsibilities across the product life cycle and supply chain.
Key dates under the CRA include:
- Sept. 11, 2026, for reporting obligations concerning actively exploited vulnerabilities and severe incidents: Manufacturers will be required to start reporting vulnerabilities and significant incidents related to their products.
- Dec. 11, 2027, for full application of the regulation: Products cannot be sold on EU markets if they don’t comply with the CRA.
Understanding the shift from RED to CRA
The RED currently includes cybersecurity requirements for internet-connected radio devices. These rules — outlined in Articles 3.3(d), (e) and (f) — focus on device security before market entry.
The CRA introduces a broader framework that applies throughout the entire product life cycle, including:
- Continuous vulnerability management
- Mandatory incident reporting within 24 hours
- Public disclosure of resolved issues
- Security-by-design and security-by-default principles
Starting Dec. 11, 2027, the CRA will replace the cybersecurity provisions of RED. This means the delegated regulation under RED (EU 2022/30) will be repealed, and manufacturers must follow CRA requirements instead.
What this means for manufacturers
Meeting RED requirements is a strong start, but the CRA calls for ongoing risk management, documentation and proactive cybersecurity maintenance beyond initial compliance.
Life Cycle Security and Vulnerability Management: The CRA’s expanded scope
Preparing for the CRA requires early engagement and relevant education through training, workshops and technical support. Explore our Guide to the Cyber Resilience Act, a practical starting point to help manufacturers prepare for the upcoming regulation. Inside, you’ll discover tools that support early preparation, especially as horizontal and vertical standards are still in development.
Preparing early for the CRA through educational initiatives helps manufacturers understand the regulatory demands, perform gap analyses and implement long-term process changes essential for sustainable compliance. Examples include training on software bills of materials (SBOMs), supply chain due diligence, threat modelling and continuous security monitoring.
Supply chain cybersecurity: A critical component of CRA readiness
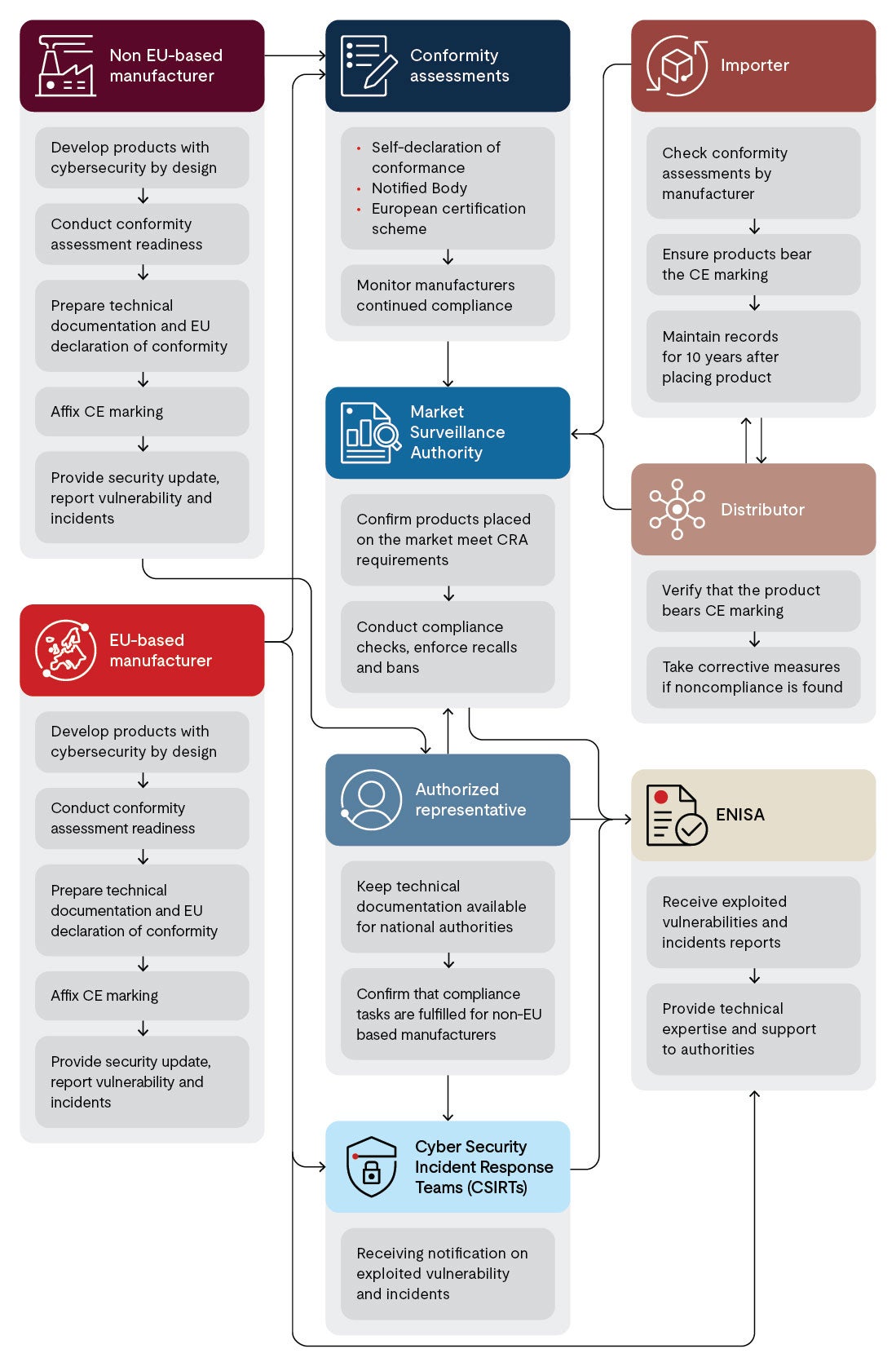
A critical aspect of CRA compliance is addressing the cybersecurity posture of the supply chain. The CRA extends obligations beyond manufacturers to include importers, distributors and all third parties in the product life cycle. Manufacturers must have supply chain visibility with relevant risk assessment and due diligence. To enforce cybersecurity compliance requirements within supply chains and networks, continuous monitoring for vulnerabilities is required. Failure to do so could expose connected networks and components to attacks, jeopardizing compliance and operational resilience.
RED compliance is a strong start — but it’s not the finish line
While meeting the RED lays a solid foundation for device security, the CRA raises the bar. It calls for a continuous, collaborative approach to cybersecurity that spans the entire product life cycle. Manufacturers must now work closely with their supply chains to close the compliance gap. That means moving quickly — engaging in training, workshops and technical support to build the knowledge and systems needed to protect both products and supply chains.
Taking action early doesn’t just support regulatory readiness — it also helps build consumer trust and protect your brand in an increasingly connected world.




