Improve your product security program
As more stringent state and industry cybersecurity regulations emerge across industries, UL Solutions understands these challenges and continues to support connected device stakeholders. SafeCyber is a security and compliance life cycle management platform hosting a suite of digitally enabled cybersecurity solutions for connected products that can help stakeholders address their cybersecurity challenges.
Device manufacturers, suppliers, system integrators and other stakeholders from chip to cloud continue to face cybersecurity challenges in today’s highly connected world. Product performance is important — but managing security and compliance is also critical.
Release more secure products faster
Stakeholders need to stay competitive and go to market quickly, but still need to maintain security and demonstrate readiness for compliance.
Mitigate product security risks
Assess the maturity of your product security processes and manage vulnerabilities.
Identify a clear path for enhancement
Discover governance, process improvements and vulnerabilities to remediate to increase the security posture of your connected products.
SafeCyber offers applications to help you develop connected products that boost compliance and manage security risks.
Why product security and compliance life cycle management can no longer be an afterthought
83%
of all businesses have experienced a firmware attack in the past two years.
Microsoft
90%
of organizations that use OT solutions fell victim to a cyberattack in the two years prior.
Ponemon Institute
85%
of businesses say security concerns are a major barrier to adopting connected devices.
Omdia and IoT World Today
A single medical device recall due to an unaddressed vulnerability can cost up to
$600 million (USD)
McKinsey
See how our suite of cloud-based security solutions empowers you
Secure development life cycle maturity assessment
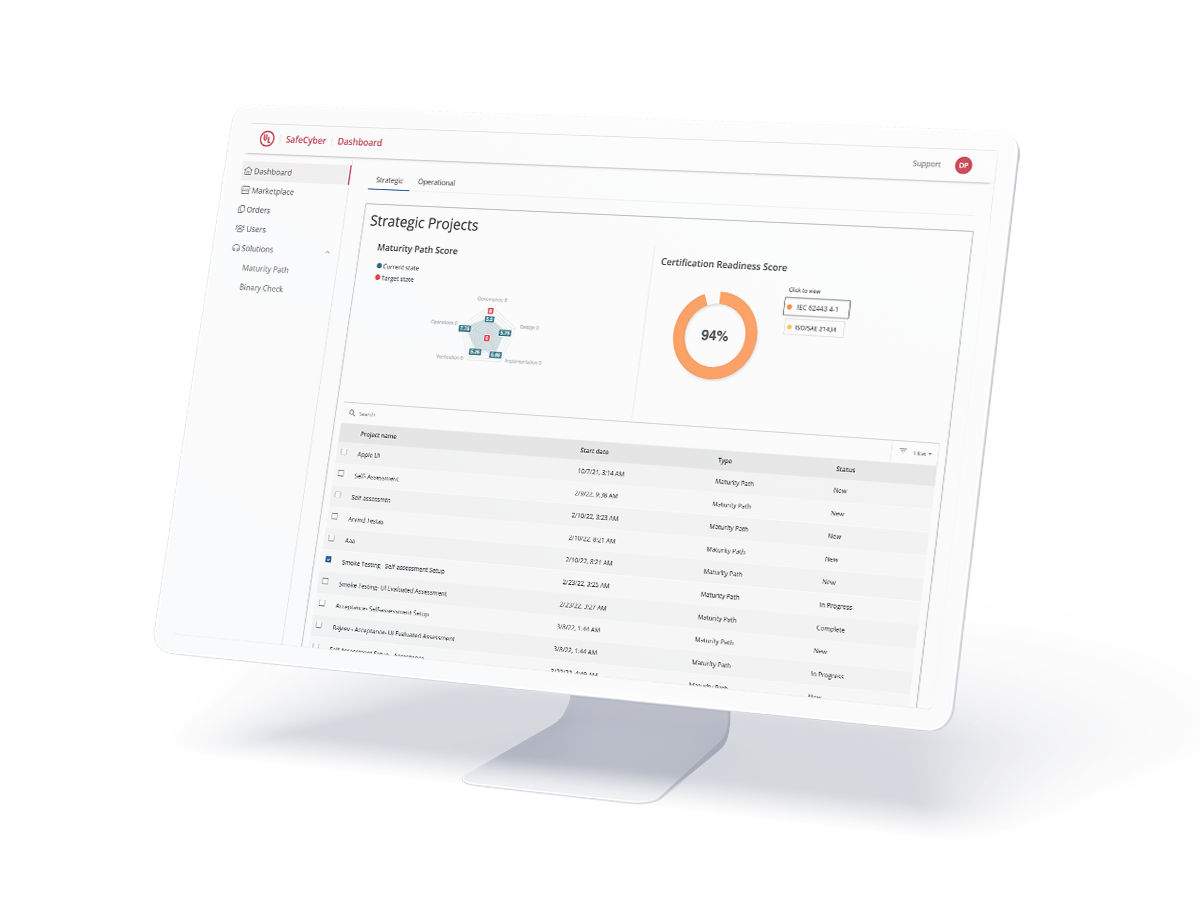
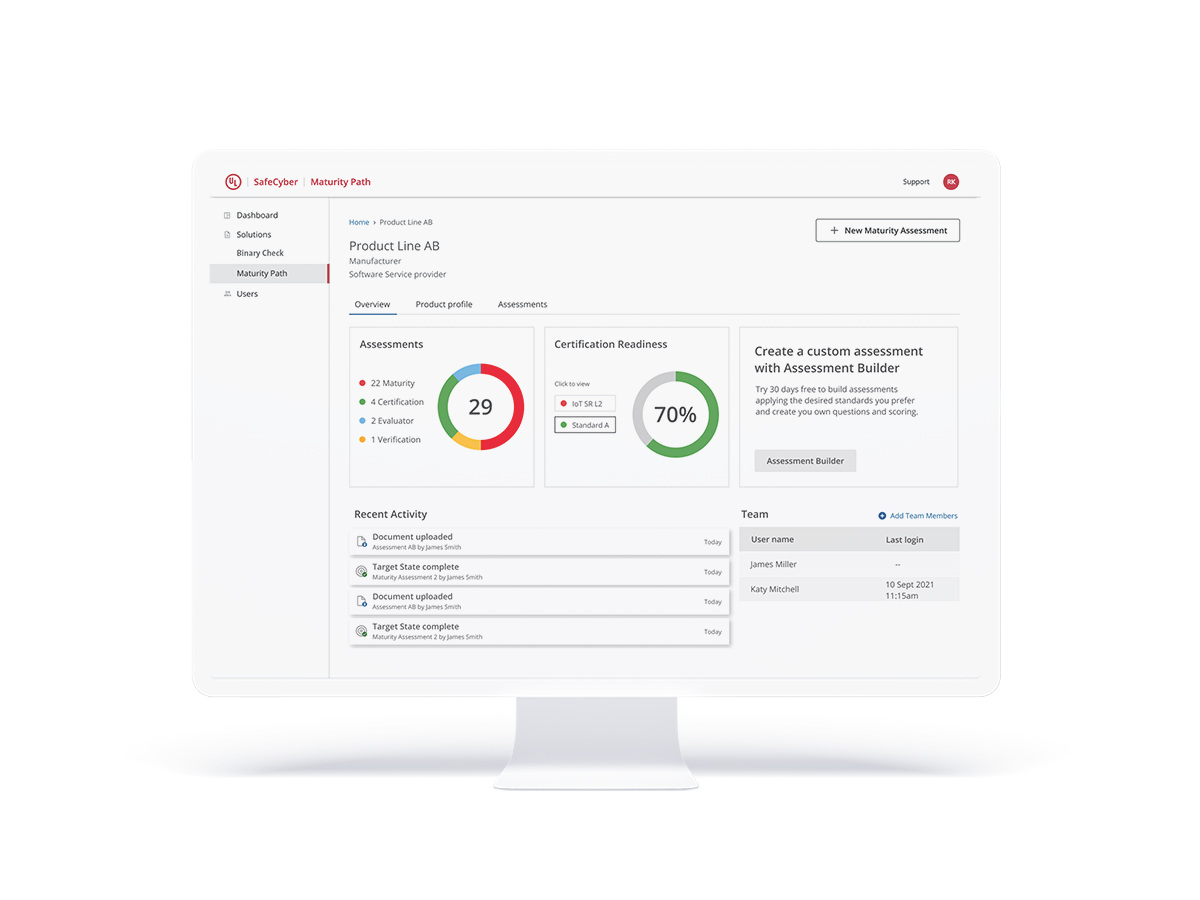
Our Maturity Path solution provides you with a secure development life cycle maturity assessment and a certification readiness score and report for your connected product lines. Conduct a complimentary self-assessment yourself or seek the expertise of one of UL Solutions' assessors. Analyze security strengths and challenges to better manage risks and minimize vulnerabilities.
Download a SafeCyber fact sheet
SafeCyber is for product security and development teams at device manufacturers, suppliers or system integrators developing connected products and looking to improve and enhance the security posture of their connected devices across the entire life cycle while speeding up time to market and helping to ensure compliance.
Have more questions about SafeCyber? Explore our Technical Guide and FAQs.
Explore SafeCyber solutions
Maturity Path
Secure development life cycle maturity and process certification readiness assessments
Request a SafeCyber Demo
Start assessing and improving your connected devices’ security posture today.