SafeCyber platform
- How can I reach out to customer support for assistance?
Once users have registered on SafeCyber and received access to the platform, they can select “Support” on the top-right side of the screen. If they cannot access the platform, they can also contact UL Solutions' technical support team at lst.ul.imsteamsafecybersupport@ul.com.
- How can I invite team members to SafeCyber platform?
The first person in a company to register on the SafeCyber account is the de facto company account administrator, who has the ability to invite team members under the same account.
A company administrator can invite other administrators or users either on the Dashboard application or directly on individual solutions such as Maturity Path by navigating to the “Users” tab on the left side and selecting “Invite new user.”
Maturity Path
- How is the maturity level scoring done?
As you complete the questionnaire, each question contributes a certain amount of points to your maturity score. The spider web diagram displays the results on the selected project page.
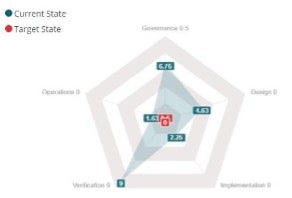
Using your answers, the tool calculates a maturity score for each subcategory (e.g., strategy and metrics within governance) and the overall category (e.g., governance) as three subcategories for the overall category. This score ranges from 0 to 3 for subcategories and 0 to 9 for the overall category.
Maturity levels and assessment scores are based on the existing Open Web Application Security Project (OWASP) Software Assurance Maturity Model (SAMM) 2.0 framework. The higher your maturity level is rated based on your given answers, the higher the score. The following table demonstrates the calculation per question and subcategory.
Assessment scores (per question) Maturity levels (per subcategory) 1
Most
3
Comprehensive mastery at scale
0.5
At least half
2
Increased efficiency and effectiveness
0.2
Some
1
Ad hoc provision
0
None
0
Practice unfulfilled
- How are certification readiness scores defined?
Certification readiness scores in Maturity Path are calculated based on an initial mapping of a standard’s clauses with the Maturity assessment questions and answers. This is how a first temporary certification readiness score is defined for available standards.
For the clauses of a standard that would not be met/mapped with the Maturity assessment, we ask additional questions so customers can determine whether they cover all clauses required from a given standard and obtain their final certification readiness score.
- Does an evaluator-led assessment provide a verification or certification?
No. Currently, an evaluator-led assessment provides a verified assessment report to the customer, which recaps all customer-provided answers and evidence along with comments made by UL Solutions' evaluator. No UL Marks will be issued as part of this service.
Get in touch
Have questions, need specifics? Let's get this conversation started.




